Deep Links SSO Integration (SAML)
The step-by-step integration mechanism required for Webassessor “Deep Links” Single-Sign On (SSO) implementation using the SAML standard.
![]()
This document outlines the step-by-step integration mechanism required for Webassessor “Deep Links” Single-Sign On (SSO) implementation using the SAML standard. This enhanced, custom SSO implementation enables client/Kryterion SSO integrations for registration or launch of an exam in Webassessor.
Use cases addressed by this enhanced SSO integration include:
Seamless candidate access to the “Instructions” page to take an exam with SSO.
Seamless candidate access to the “Testing Center selection” page (KTN) with SSO.
Seamless candidate access to the “Calendar” page (OLP) with SSO.
All of the preceding options can be supported by the same SSO call. Client needs will dictate which parameters are passed in the SSO call. The integration specification will be generic enough to accommodate most clients’ needs as of December 5, 2023.
References
[SAML]: The SAML specification documentation is available at: http://saml.xml.org/saml-specifications
Prerequisites
Clients wishing to integrate with Webassessor SSO using SAML specs should either have a properly configured SAML Identity Provider (IdP) server in-house or be able to use a 3rd party IdP like Okta, Salesforce, etc.
Webassessor must list the applicable client (entity), the associated client region, and client brand since they are part of communication during SSO calls.
Integration Points and Flows
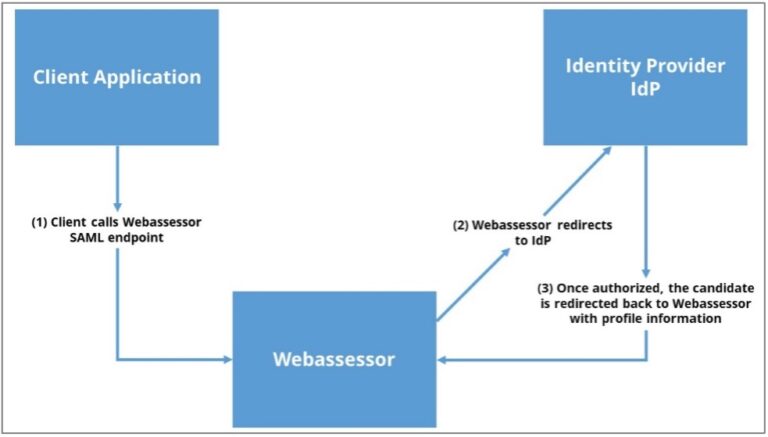
Implementation Steps
Step 1: Client provides the SAML Identity Provider (IdP) server details to Kryterion
Before an integration can be set up, the client must provide SAML IdP server details (URL & login information) to Kryterion. During the configuration of the metadata URL from the client, please make sure the entity id within this file matches the IDP URL they provide. The data allows Kryterion to register Webassessor as an application authorized to access the client’s User Profile information. The authorization enables communication with the client’s IdP server.
Metadata URI | Metadata URL address of SAML IdP server that will provide authorization |
IDP ID/URI | Identity URL address of SAML IdP server that will provide authorization |
Step 2: Client adds Webassessor information into their system
SSO URI
Production: https://www.webassessor.com/SsoService/saml/SSO
Metadata URL
Sandbox: https://sb01.webassessor.com/SsoService/saml/metadata
Production: https://www.webassessor.com/SsoService/saml/metadata
Step 3: Client uses the following links to initiate the SSO workflow
Sandbox: https://sb01.webassessor.com/SsoService/doSaml ? provider={PROVIDER}&brand={BRAND}&postLoginParams={POSTLOGINPARAMS}
Production: https://www.webassessor.com/SsoService/doSaml ? provider={PROVIDER}&brand={BRAND}&postLoginParams={POSTLOGINPARAMS}
{PROVIDER} and {BRAND} values are unique to each Client
{POSTLOGINPARAMS} are:
For Registering for an Exam:
REGISTER-SCHEDULE-{EXAM ID}-PROCTORED-USD-100.00
For Rescheduling an Exam Registration:
REGISTER-RESCHEDULE-{REG ID}
For Cancelling an Exam Registration:
REGISTER-CANCELLATION-{REG ID}
For Launching an Exam Registration:
LAUNCH-{REG ID}
PARAMETER | SUPPLIED BY | DESCRIPTION | MANDATORY | EXAMPLES |
provider | Webassessor | A unique name saved in the Webassessor database to identify client | YES | companyx, companyz |
brand | Webassessor | The client’s brand name created in Webassessor | YES | COMPANYX, COMPANYZ |
postLoginParams | client | This is used for post login actions | YES | REGISTER- |
|
| such as registration or launching an |
| SCHEDULE- |
|
| exam. The separator is the “^” sign |
| 123456-KTN- |
|
| to parse the incoming parameters. |
| USD-100.00 |
|
| Registration: |
| REGISTER- RESCHEDULE- |
|
| For Registration after Login, |
| 123456 |
|
| accepted parameter combinations & scenarios: REGISTER-SCHEDULE- EXTERNAL_REFERENCE_ID- DELIVERY_TYPE- |
| REGISTER- CANCELLATION- 123456 LAUNCH-123456 |
|
| CURRENCY-PRICE |
|
|
|
| REGISTER-RESCHEDULE- |
|
|
|
| REGISTRATION_ID |
|
|
|
| REGISTER-CANCELLATION- |
|
|
|
| REGISTRATION_ID |
|
|
|
|
Notes: |
|
|
|
| SCHEDULE call – |
|
|
|
| “EXTERNAL_REFERENCE_ID” |
|
|
|
| is whatever is set at the product |
|
|
|
| level in Webassessor. |
|
|
|
| RESCHEDULE call – |
|
|
|
| REGISTRATION_ID should be |
|
|
|
| the “REGISTRATION_ID” of the |
|
|
|
| registration in Webassessor |
|
|
|
| (This will be available to the |
|
|
|
| clients as a result of the “Add |
|
|
|
| Registration” Webservice they |
|
|
|
| will use to create the |
|
|
|
| registration in Webassessor or |
|
|
|
| “Get Registration” call they |
|
|
|
| make at the end of SSO |
|
|
|
| “SCHEDULE” call above). |
|
|
|
| CANCEL call – |
|
|
|
| REGISTRATION_ID should be |
|
|
|
| the “REGISTRATION_ID” of the |
|
|
|
| registration in Webassessor |
|
|
|
| (This will be available to the |
|
|
|
| clients as a result of the “Add |
|
|
|
| Registration” Webservice they |
|
|
|
| will use to create the |
|
|
|
| registration in Webassessor or |
|
|
|
| “Get Registration” call they |
|
|
|
| make at the end of SSO |
|
|
|
| “SCHEDULE” call above). |
|
|
|
|
Launch: |
|
|
|
| For Launch after Login, accepted |
|
|
|
| parameter combinations |
|
|
|
| “LAUNCH-REGISTRATION_ID“ |
|
|
|
| Notes: |
|
|
|
| “REGISTRATION_ID” for launch |
|
|
|
| will always be the |
|
|
|
| “REGISTRATION_ID” of the |
|
|
|
| registration in Webassessor (This |
|
|
|
| will be available to the clients as a |
|
|
|
| result of the “Add Registration” |
|
|
|
| Webservice they will use to create |
|
|
|
| the registration in Webassessor or |
|
|
|
| “Get Registration” call they make at |
|
|
|
| the end of SSO “SCHEDULE” call |
|
|
|
| above). |
|
|
Here is an in-depth explanation of POSTLOGINPARAMS
Registration related Parameters explanation:
VARIABLE | DEFINITION |
REGISTER | This value is always REGISTER and indicates that the post login action is Registration. |
SCHEDULE, RESCHEDULE, CANCEL | Acceptable values in the call above |
CLIENT_PRODUCT_UNIQUE_ID | This is the unique external reference id of the product. Clients can provide this when creating a product in Webassessor. |
DELIVERY_TYPE | Delivery Type of the intended exam registration. Expected Values: KTN, OLP, NP |
CURRENCY | Currency of the amount. Accepted Values: USD, EUR, GBP, JPY, CAD, AUD |
PRICE | Price of the exam. (If price is not applicable then a default of “0.00” should be sent). Example: 23 or 23.0 or 23.00 |
Launch related parameters explanation:
VARIABLE | DEFINITION |
LAUNCH | This value is always LAUNCH and indicates that the post login action is Launching an exam. |
REGISTRATION_ID | Registration id of the exam that needs to be launched. |
Once the control reaches Webassessor, Webassessor initiates SAML authentication by calling the IdP using the details configured on our end. On the IdP login page, once the candidate provides their login information and is successfully logged in, the IdP redirects back to Webassessor with the candidate’s profile information.
Using profile information obtained in the previous step, Webassessor retrieves the user profile and logs the user into our application.
Step 4: (Optional) Client provides a Redirect URL to redirect candidates after they complete the transaction
This feature is purely for user continuity and is candidate experience related. It is designed for clients that want their candidates returned to their application following candidate completion of the Deep Links-targeted Webassessor transaction.
The Webassessor SSO configuration page parameter “Client Redirect URL,” when populated, allows Kryterion to redirect candidates immediately upon completion of the targeted Webassessor transaction. When no value is given for the Client Redirect URL during setup, the candidate will be logged out of Webassessor as the last step. The Client Redirect URL must be a client-specified, standard URL.
Access to certain features is restricted based on role type in an effort to reduce item exposure and promote process integrity. Please see the member role description page for information on permissions.
