Standard SSO Integration (SAML)
Outlining Webassessor Single-Sign-On (SSO) integration using Security Assertion Markup Language (SAML) instead of OAuth2.
![]()
This document outlines Webassessor Single-Sign-On (SSO) integration using Security Assertion Markup Language (SAML) instead of OAuth2. Both approaches are offered by Kryterion, Inc. to its clients.
Before implementing SAML into Webassessor it is important to understand that SAML, unlike OAuth2, has just two entities,
Identity Provider (IdP) – Always the Client.
Service Provider (SP) – Always Webassessor.
The following high-level overview of Kryterion’s standard Webassessor SSO integration using SAML summarizes the applicable implementation integration points and boundaries.
References:
[SAML]: The SAML specification documentation is available at: http://saml.xml.org/saml-specifications
Pre-requisites:
Since the SSO follows SAML specification, in order for a client to be able to effectively integrate with Webassessor for SSO, the client should either have an in-house IdP server or should be able to use a 3rd party IdP like Okta, Salesforce, etc.
Client should be created in the Webassessor system as an entity and region with a brand since they are part of communication during SSO calls.
Integration Points and Flows
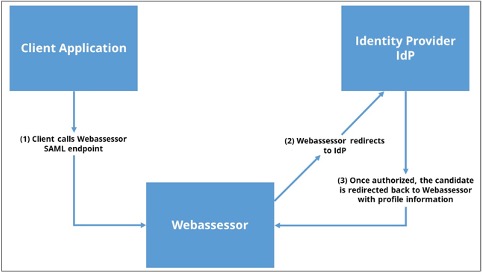
Implementation Steps
Step 1: Client provides the SAML IdP server details
Before the integration can be set up, Kryterion’s Webassessor system needs certain values in order to communicate with the client IdP (Identity Provider) server. The client will provide SAML IdP server details (URL & login information) for Kryterion to register Webassessor as an application authorized to have access to the client’s User Profile information.
Metadata URI | Metadata URL address of SAML IdP server that will provide authorization |
IDP ID/URI | Identity URL address of SAML IdP server that will provide authorization |
Step 2: Client adds Webassessor information into their system
SSO URI:
Metadata URL:
Step 3: Client uses the following links to initiate the SSO workflow
Sandbox: https://sb01.webassessor.com/SsoService/doSaml?provider={PROVIDER}&brand={BRAND}
Production: https://www.webassessor.com/SsoService/doSaml?provider={PROVIDER}&brand={BRAND}
{PROVIDER} and {BRAND} values are unique to each Client
Access to certain features is restricted based on role type in an effort to reduce item exposure and promote process integrity. Please see the member role description page for information on permissions.
